Introduction to Phishing
Phishing is a cyberattack where the attacker tricks the target into disclosing personal information, revealing login credentials, or transferring money. Occurring predominantly via email, phishing is typically bulk in nature and not personalized for an individual target. These scams often come in the form of seemingly harmless emails from your bank or text messages announcing that you’ve won a prize. By exploiting your trust and triggering fear, phishing attempts aim to steal your personal information.
Phishing attacks have become one of the most common and harmful types of cybercrime, affecting both individuals and organizations. As these tactics become increasingly sophisticated, it’s essential to learn how to recognize and avoid them. This guide will provide you with all the necessary information about phishing, including the various types of scams and practical tips for safeguarding yourself online.
1. Types of Phishing Attacks
Phishing comes in many forms, each designed to exploit different vulnerabilities in how we communicate and use the internet. While traditional email phishing, where attackers impersonate trusted organizations to steal sensitive information, is well-known, tactics have evolved to include targeted spear phishing and scams via text messages and phone calls. Recognizing the various types of phishing attacks is crucial for effective defense against them.
Email Phishing
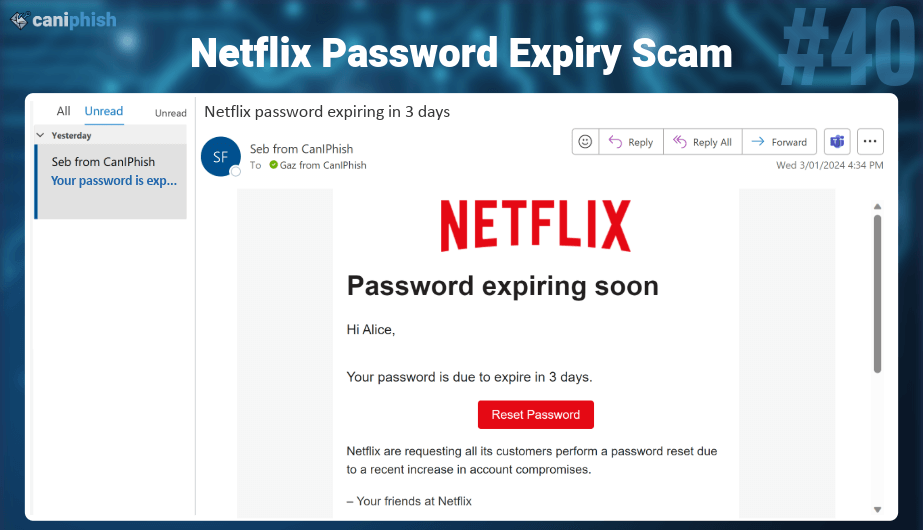
Email phishing, or deceptive phishing, is a popular type of cyberattack in which attackers attempt to steal their victims’ sensitive information via email. The emails will often contain a malicious link that redirects users to a phishing web page. The attackers might also attach an unknown document containing malware.
Spear Phishing
Spear phishing is a kind of phishing attack that targets one person (or company) in particular. The attackers try to get as close to their target as possible and then send them an email that appears very official.
Spear-phishers often invest considerable effort into researching their targets before launching an attack. They will identify key individuals responsible for various projects or departments within the target organization. In some cases, they may even reach out to employees at the same company to build rapport, making their eventual scam appear more credible and legitimate. Take the case of MacEwan University that got duped out of $11.8 million by scammers.
Smishing (SMS Phishing)
Smishing scams are similar to email phishing scams, but they use text messages instead of emails. In these scams, the fraudster sends a text that appears to come from a trustworthy source, like a bank or a government agency. Typically, the message will urge the recipient to click on a link or share personal information. If the victim follows through, the scammer can exploit their details for various fraudulent purposes.
Vishing (Voice Phishing)
Vishing, or voice phishing, is a phone call scam used to trick victims into sharing their personal information. Cybercriminals use various approaches, like warning users that their account has been compromised or announcing that the targeted user has won a type of reward or lottery.
Clone Phishing
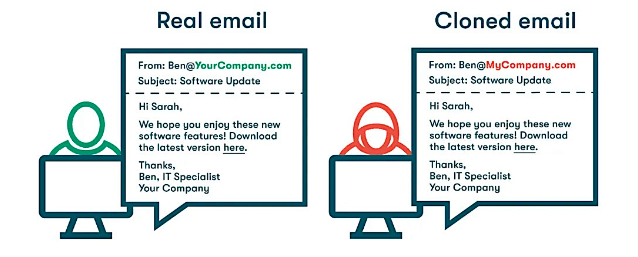
Clone phishing is a deceptive technique where attackers duplicate a legitimate email that was previously sent by a trusted source, such as a company or colleague, and modify it with malicious intent. The attacker uses the same content, design, and sender details as the original email, but swaps out legitimate links or attachments for malicious ones.
2. Common Phishing Tactics
Phishing scams often rely on psychological manipulation and technical deception to trick victims into revealing sensitive information. Understanding these tactics can help you recognize a scam before it’s too late. Here are some of the most common methods used by attackers:
Urgency and Fear
Phishers often create a sense of panic or urgency to force quick decisions. They may claim your account is compromised, your payment has failed, or you’ve missed an important deadline, pressuring you to act without thinking.
Spoofed Email Addresses and URLs
Scammers often use email addresses or websites that closely resemble those of legitimate organizations by making minor changes, such as replacing an “m” with an “rn” or altering the domain slightly (e.g., “example.com” becomes “examp1e.com”). These small differences can be easy to overlook.
Fake Login Pages
Attackers may direct you to websites that look almost identical to the real ones, designed to steal your login credentials once you enter them. Always double-check the URL and security certificates before entering sensitive information.
Malicious Attachments
Be cautious of emails that appear to have legitimate attachments; they could actually be hiding malware or viruses. When these files are downloaded, they can compromise your device, giving attackers the ability to access your personal information or take control of your system.
Impersonation of Trusted Sources
Cybercriminals frequently impersonate individuals you might recognize, such as coworkers, managers, or reputable organizations. By taking over email accounts or creating look-alike email addresses, they can make their communications seem credible and trustworthy.
By familiarizing yourself with these tactics, you can spot red flags early and avoid falling victim to phishing scams.
Phishing in Action: Notable Scams
Colonial Pipeline (up to €3.4 billion)
In May 2021, millions of Americans experienced first-hand the damage that cyberattacks can cause, after fuel supplier Colonial Pipeline was crippled by a ransomware attack. The organization was forced to halt operations after its business network and billing system were compromised.
Although ransomware was responsible for much of the damage, the attackers were only able to plant the malicious software after gaining access to an employee’s password—most likely through a phishing email. As the US government noted, the DarkSide gang responsible for the attack has used such methods.
The breach’s cost is difficult to determine fully. Colonial Pipeline paid the attackers $4.4 million (about €3.75 million) for the decryption key, but that was just the tip of the iceberg. The organization, which provides almost half of the oil supplies to the east coast of the US, was shut down for a week, resulting in the non-delivery of about 20 billion gallons of oil, worth approximately €3.4 billion at the time. This caused a spike in petrol prices, passing some of the costs onto the public. The combined damage to Colonial Pipeline and the US economy makes this by far the most expensive phishing attack ever seen.
3. Protecting Yourself from Phishing Attacks
Taking a proactive approach is key to safeguarding yourself from phishing attacks. Here are some essential steps you can take to reduce your risk:
Verify Before Clicking
Always double-check email addresses and URLs for authenticity before clicking on links. Slight variations can indicate a phishing attempt.
Use Anti-Phishing Software
Install browser extensions or security software that can detect and block phishing attempts.
Enable Two-Factor Authentication (2FA)
Adding an extra layer of security through 2FA makes it much harder for attackers to access your accounts.
Regularly Update Passwords
Strong, unique passwords reduce the risk of account compromise. Consider using a password manager.
Malicious Link Checkers
Use online tools to verify suspicious links before clicking on them to avoid falling into phishing traps.
Be Sceptical of Unsolicited Requests
Always question unexpected emails or messages, especially those asking for sensitive information.
Phishing scams are becoming increasingly sophisticated, but with awareness and the right precautions, you can protect yourself from falling victim. By recognizing common phishing tactics and implementing security measures like verifying links, enabling two-factor authentication, and using anti-phishing tools, you can safeguard your personal information. Stay vigilant, trust your instincts, and always think before you click.