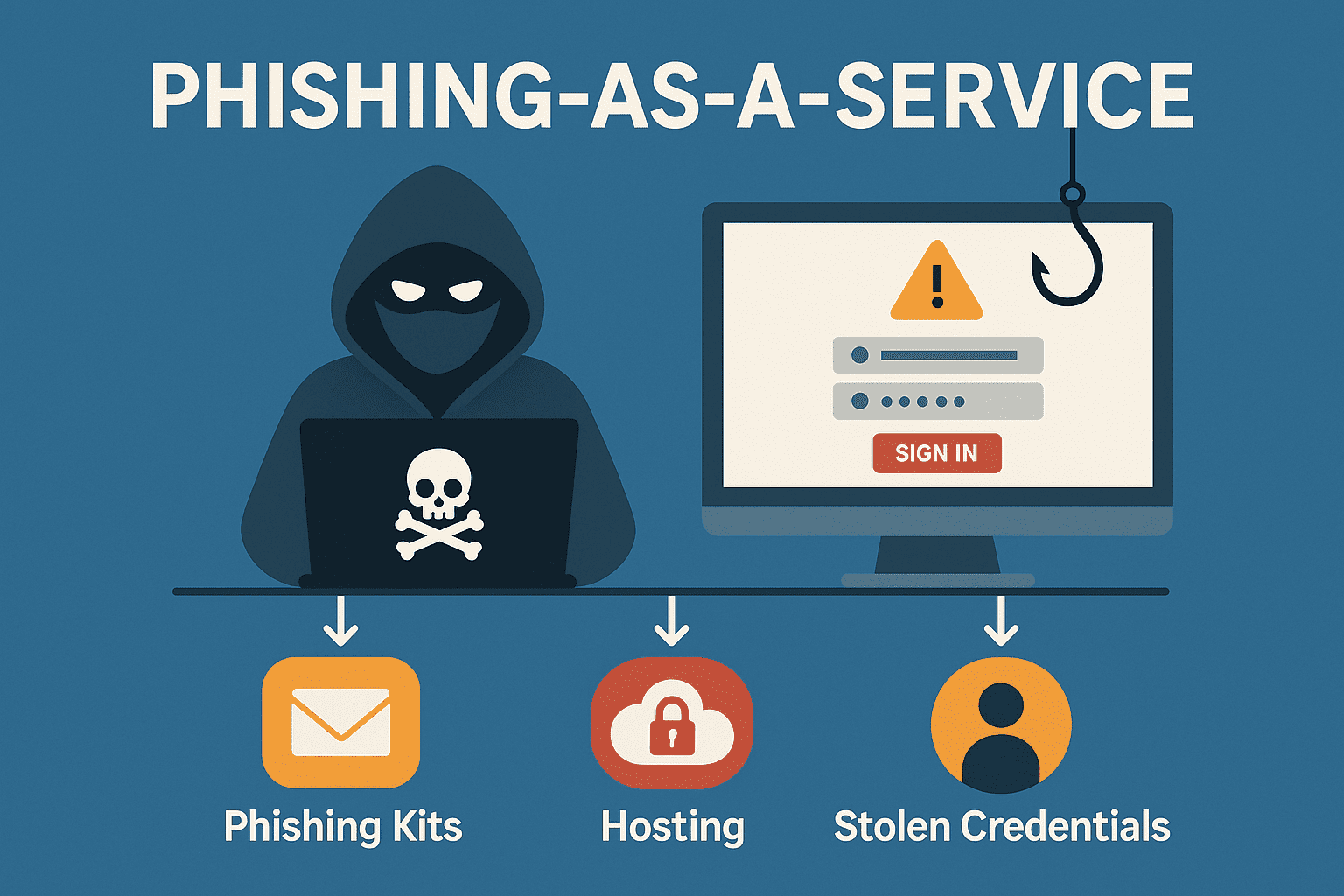
In 2025, phishing is no longer the domain of skilled hackers. Thanks to Phishing-as-a-Service (PhaaS), anyone—even with zero technical expertise—can launch convincing, large-scale phishing attacks for a small fee. This underground market has exploded in popularity, reshaping the cybercrime economy and complicating efforts to defend against malicious campaigns.
What is PhaaS?
Phishing-as-a-Service is a business model where cybercriminals sell or rent out phishing toolkits, templates, and infrastructure to other bad actors. Think of it as SaaS (Software-as-a-Service) for hackers: complete with dashboards, customer support, updates, and even success analytics.
Clients pay for:
- Pre-designed phishing websites mimicking banks, SaaS apps, or email platforms.
- Email spam tools or SMS delivery platforms.
- Hosting infrastructure (often via bulletproof hosting).
- Access to stolen credential databases.
- Custom AI tools that craft realistic messages.
A report by The Wall Street Journal says: We’re seeing a rise in professionalized phishing services—complete with tiered pricing, loyalty discounts, and even customer testimonials
What Makes PhaaS So Dangerous?
1. Low Barrier to Entry
Anyone with cryptocurrency and access to the dark web can launch phishing attacks. No coding skills required.
2. AI Integration
Many PhaaS platforms now include AI-powered tools to generate personalized emails and clone websites quickly.
3. Scale and Automation
Some services let attackers deploy tens of thousands of phishing messages across email, SMS, and social media in seconds.
4. Bulletproof Hosting
These platforms rely on offshore or anonymous hosting providers that ignore takedown requests, making phishing sites harder to remove.
Real-World Impact
- Credential Harvesting: Enterprises are increasingly seeing phishing emails generated by PhaaS platforms that mimic internal messages—down to logos, writing style, and sender aliases.
- Brand Damage: Fake login portals hosted by PhaaS tools often replicate big brands like Microsoft, Google, and financial institutions, tricking users and tarnishing corporate reputations.
- Ransomware Entry Point: Some PhaaS kits are bundled with initial access brokers, meaning stolen credentials are sold or used for larger ransomware campaigns.
How to Defend Against PhaaS-Driven Attacks?
1. Advanced Threat Detection
- Use behavioral analysis and machine learning–based email filters.
- Block emails with suspicious URLs, domains, or mismatched sender info.
2. DMARC, SPF, and DKIM
- Implement proper email authentication protocols to prevent spoofing.
3. User Awareness
- Conduct ongoing phishing simulations and awareness training.
- Train users to verify senders, URLs, and avoid scanning unsolicited QR codes.
4. Monitor the Dark Web
- Watch for leaked credentials tied to your organization and report impersonation attempts.
Phishing-as-a-Service has transformed phishing from an art to an industry. The increasing professionalization of cybercrime means that even unsophisticated actors can carry out advanced phishing attacks, making it critical for organizations to adopt multi-layered defenses.
As these services grow in complexity and availability, staying ahead of attackers will require the same level of innovation and adaptability from defenders.